Created by Nguyen Kim Son
1. Introduction
Network Address Translation - NAT is a method of remapping one IP address space into another by modifying network address information in Internet Protocol datagram, may also TCP/UDP port numbers.
As IPv4 Addresses are 32 Bit, in theory we could have upto 4,294,967,296 IP Addresses (2^32). Although IPv4 was capable of uniquely addressing more than 4 billion devices, and that IPv4 was not going to be able to extend across the full range of future device deployment.
The objective with NAT was to define a mechanism that allowed IP addresses to be shared across numerous devices.
2. Basic NAT Operation
The basic NAT operation is demonstrate in figure 1. NATs intercept all IP packets, and may forward the packet onward with or without alteration to the contents of the packet, or may elect to discard the packet. NATs are similar to firewalls, and different from routers, in that they are topologically sensitive. They have an "inside" and an "outside," and undertake different operations on intercepted packets depending on whether the packet is going from inside to outside, or in opposite direction.
Figure 1. Basic NAT operation
The idea is create a range of private IPs that are separate from the rest of the network. The private IPs is used for internal routing, and it is not globally unique. Typical private IP ranges are:- 10.0.0.0 - 10.255.255.255
- 172.16.0.0 - 172.31.255.255
- 192.168.0.0 - 192.168.255.255
The basic NAT operation is demonstrate in figure 1. NATs intercept all IP packets, and may forward the packet onward with or without alteration to the contents of the packet, or may elect to discard the packet. NATs are similar to firewalls, and different from routers, in that they are topologically sensitive. They have an "inside" and an "outside," and undertake different operations on intercepted packets depending on whether the packet is going from inside to outside, or in opposite direction.
NATs are IP header translators, and in particular, NATs are IP address translators.
The header of an IP packet contains the source and destination IP addresses. If the packet is being passed in the direction from the inside to the outside, a NAT rewrites the source address and port number in the packet header to a different value, and alters the IP and TCP header checksums in the packet at the same time to reflect the change of the address field. When a packet is received from the outside destined to the inside, the destination address is rewritten to a different value, and again the IP and TCP header checksums are recalculated.
3. NAT Types
There are several ways of implementing network address and port translation. All types of NAT fall into two categories: Static NAT and Dynamic NAT. Static NAT is where administrators manually create and maintain the NAT mappings and is usually associated with inbound types of NAT. Dynamic NAT is where the router creates and maintains mappings automatically on demand and is usually associated with outbound types of NAT.The Simple traversal of UDP over NATs (STUN) protocol was developed (RFC 3489, March 2003) classified NAT implementation as full-cone NAT, restricted-cone NAT, port-restricted cone NAT and symmetric NAT.
Full-cone NAT (Static NAT)
There are several ways of implementing network address and port translation. All types of NAT fall into two categories: Static NAT and Dynamic NAT. Static NAT is where administrators manually create and maintain the NAT mappings and is usually associated with inbound types of NAT. Dynamic NAT is where the router creates and maintains mappings automatically on demand and is usually associated with outbound types of NAT.The Simple traversal of UDP over NATs (STUN) protocol was developed (RFC 3489, March 2003) classified NAT implementation as full-cone NAT, restricted-cone NAT, port-restricted cone NAT and symmetric NAT.
Full-cone NAT (Static NAT)
Figure 2. Full Cone NAT
- Once an internal address (iAddr:iPort) is mapped to an external address (eAddr:ePort), any packets from iAddr:iPort are sent through eAddr:ePort.
- Any external host can send packets to iAddr:iPort by sending packets to eAddr:ePort
- Example – My PC has a website running on port 80. I create a one-to-one rule that maps the router WAN IP of 81.45.87.98 to 192.168.0.1 with port 80 to port 80. Any external host that sends data to 81.45.87.98 on port 80 is NATed (and sent) to 192.168.0.1 port 80.
Note: the port numbers do not have to be the same; I could run my website on port 56456 but create the NAT mapping to forward port 80 to port 56456. This gives the appearance to the public Internet that my website is on port 80. A connection attempt on any other port is dropped.
Figure 3. Restricted Cone NAT
- Once an internal adddress (iAddr:iPort) is mapped to an external address (eAddr:ePort), any packets from iAddr:iPort are sent through eAddr:ePort.
- An external host (hAddr:any) can send packets to iAddr:iPort by sending packets to eAddr:ePort only if iAddr:iPort has previously sent a packet to hAddr:any. "Any" means the port number doesn't matter.
- Example – My PC makes an outbound connection to a website (56.45.34.78) with my source IP 192.168.0.1 and source port 56723. The NAT creates a (dynamic) mapping to my PC using source port 56723. Packets that arrive with a source IP of 56.45.34.78 (the website IP) using a destination port of 56723 (which was the outbound NATed source port) will be accepted and sent to my PC. Connection attempts from any other IP using the correct port of 56723 will be dropped. Connection attempts from the correct IP with a destination port other than 56723 will also be dropped.
Figure 4. Port Restricted Cone NAT
- Like an address restricted cone NAT, but the restriction includes port numbers
- Once an internal address (iAddr:iPort) is mapped to an external address (eAddr:ePort), any packets from iAddr:iPort are sent through eAddr:ePort.
- An external host (hAddr:hPort) can send packets to iAddr:iPort by sending packets to eAddr:ePort only if iAddr:iPort has previously sent a packet to hAddr:hPort.
- Example – My PC makes an outbound connection to website IP 217.87.69.8 on port 80 (destination port). The NAT maps my source IP 192.168.0.1 to the WAN IP of 81.45.87.98 and source port 56723. When the website sends packets back it must have it’s source IP as 217.87.69.8, destination port as 56723 (like a restricted cone NAT) but in addition the source port must be 80. If any of these three are different a port restricted cone NAT drops the connection
Figure 5. Symmetric NAT
- Each request from the same internal IP address and port to a specific destination IP address and port is mapped to a unique external source IP address and port; if the same internal host sends a packet even with the same source address and port but to a different destination, a different mapping is used.
- Only an external host that receives a packet from an internal host can send a packet back
4. NAT Traversal
NAT traversal is a computer networking methodology with the goal of establishing and maintaing Internet protocol connections across gateways that implement network address translation - NAT. NAT traversal techniques are required for certain client-to-client network applications, such as peer-to-peer file sharing and VoIP.
The NAT traversal problem arises when two peers behind distinct NAT try to communicate. In a P2P application, any participating Peer A should be able to initiate a TCP connection to any other participating Peer B. The essence of the problem is that if Peer B is behind a NAT, it cannot act as a server and accept TCP connections.
There are several ways to resolve this problem, such as: Port forwarding, Port triggering, Universal Plug and Play - UPnP, Session Traversal Utilities for NAT - STUN, Traversal Using Relays around NAT - TURN.
NAT traversal is a computer networking methodology with the goal of establishing and maintaing Internet protocol connections across gateways that implement network address translation - NAT. NAT traversal techniques are required for certain client-to-client network applications, such as peer-to-peer file sharing and VoIP.
The NAT traversal problem arises when two peers behind distinct NAT try to communicate. In a P2P application, any participating Peer A should be able to initiate a TCP connection to any other participating Peer B. The essence of the problem is that if Peer B is behind a NAT, it cannot act as a server and accept TCP connections.
Figure 6. NAT Traversal Problem
In Figure 6., client wants to connect to server with address 10.0.0.1. But the problem is that server address 10.0.0.1 is in local LAN network (client can't use this address as destination address), only one externally visible NATed address 138.76.29.7. How client can connect to this server?There are several ways to resolve this problem, such as: Port forwarding, Port triggering, Universal Plug and Play - UPnP, Session Traversal Utilities for NAT - STUN, Traversal Using Relays around NAT - TURN.
4.1. Port Forwarding
Port Forwarding is an application of NAT that redirect a communication request from one address/port to another while the packets are traversing a network gateway, such as a router or firewall. Port forwarding allows remote computers to connect to a specific computer or service within a private local-area network (LAN).
When configuring port forwarding, the network administrator sets aside one port number on the gateway for the exclusive use of communicating with a service in the private network, located on a specific host. External hosts must know this port number and external address of gateway to communicate with the network-internal service. Often, the port numbers of well-known Internet services, such as port number 80 for HTTP, are used in port forwarding.
Port Forwarding is an application of NAT that redirect a communication request from one address/port to another while the packets are traversing a network gateway, such as a router or firewall. Port forwarding allows remote computers to connect to a specific computer or service within a private local-area network (LAN).
When configuring port forwarding, the network administrator sets aside one port number on the gateway for the exclusive use of communicating with a service in the private network, located on a specific host. External hosts must know this port number and external address of gateway to communicate with the network-internal service. Often, the port numbers of well-known Internet services, such as port number 80 for HTTP, are used in port forwarding.
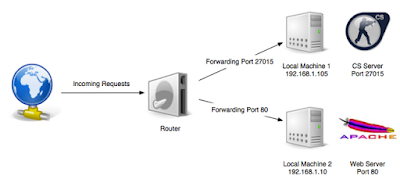
Figure 7. Port Forwarding Operation
Typical applications include the following:- Running a public HTTP server within a private LAN
- Permitting Secure Shell access to a host on the private LAN from the Internet
- Permitting FTP access to a host on a private LAN from the Internet
- Running a publicly avaiable game server within a private LAN
A lot of multiplayer video games (as an example, Counter Strike) allow you to run a game server on your computer that other people can connect to in order to play with you. Your computer doesn't know all the people that want to play, so it can't connect to them - instead, they have to send new connection requests to your computer from the internet. If you didn't have anything set up on the router, it would receive these connection requests but it wouldn't know which computer inside the network had the game server, so it would just ignore them (or, more specifically, it would send back a packet indicating that it can't connect). Luckily, you know the port number that will be on connection requests for the game server. So, on the router, you set a port forward with the port number that the game server expects (for example, 27015) and the IP address of the computer with the game server (for example, 192.168.1.105).
The router will know to forward the incoming connection requests to 192.168.1.105 inside the network, and computers outside will be able to connect in.
Another example would be a local network with two machines, where the second one with the IP 192.168.1.10 hosts a website using Apache. Therefore the router should forward incoming port 80 requests to this machine. Using port forwarding, both machines can run in the same network at the same time.
The router will know to forward the incoming connection requests to 192.168.1.105 inside the network, and computers outside will be able to connect in.
Another example would be a local network with two machines, where the second one with the IP 192.168.1.10 hosts a website using Apache. Therefore the router should forward incoming port 80 requests to this machine. Using port forwarding, both machines can run in the same network at the same time.
Figure 8. Port Forwarding examples
4.2. Universal Plug and Play - UPnPUniversal Plug and Play (UPnP) is a set of networking protocols, was promoted by the UPnP forum, that permits networked devices, such as PC, printers, mobile devices ... to discover each other's presence on the network and establish functional network services for data sharing, communication, and entertainment.
UPnP protocol allows NATed host to learn public IP address, and automatically add/remove port mappings with lease times.
UPnP works the exact same way as port forwarding. Instead of setting up manually, software on a computer inside the network automatically sets the router to forward traffic on a given port to it.
4.3. Session Traversal Utilities for NAT - STUN
NATs provide a device with an IP address for use within a private local network, but this address can't be used externally. Without a public address, there's no way for network devices to communicate.
STUN is a client-server network protocol to allow an application running on a host to determine whether or not it is located behind a network device that is performing address translation.
Problems with STUN
STUN is only useful in certain situations when one peer is behind a symmetric NAT, and other peer is not. STUN does not useful when both peers are fully behind symmetric NATs.
NATs provide a device with an IP address for use within a private local network, but this address can't be used externally. Without a public address, there's no way for network devices to communicate.
STUN is a client-server network protocol to allow an application running on a host to determine whether or not it is located behind a network device that is performing address translation.
Figure 9. STUN Operation
The basic protocol operates as follows: the client sends a message to a STUN server on the public Internet. The STUN server responds with a success response that contains in its payload the IP address and port of the client (external IP address and external port).STUN messages are usually sent in UDP packets. Since UDP does not provide reliable transport guarentees, the TCP packets may be used.
Figure 10. P2P application with STUN
STUN is used to resolve the problem of P2P application when both peer are behind NAT. Firstly, both peer communicate with STUN server to get the external IP address and external port. Secondly, both peer wrap IP address and port into signalling packets and using some signalling protocol to send these packets. After that, both peer get the IP/Port of each other. From now, peers can communicate with each others. The signalling protocol often used are SIP or H323 protocol.Problems with STUN
STUN is only useful in certain situations when one peer is behind a symmetric NAT, and other peer is not. STUN does not useful when both peers are fully behind symmetric NATs.
Figure 11. Problems with STUN
STUN and Port Restricted NAT- My console with IP address 192.168.0.1 hosts a game using port 57433. It connects to xbox live to advertise this information.
- Xbox live (using STUN) detects my public IP address of 56.45.32.5 and public port of 57433 and informs my console of this.
- My console updates this information and advertises these details on xbox live.
- Another person browses xbox live for my game. Once he clicks “join” his console retrieves my public IP address and port and attempts to connect directly. It tries to connect on 56.45.32.5 with port 57433.
- The initial connection will be blocked by a port restricted NAT because I haven’t yet sent any data to that console. My console now sends data to the remote console (IP and port learnt through xbox live) using source port 57433 with source IP 5.45.32.5.
- All subsequent packets sent from the remote console to 56.45.32.5 using port 57433 will now be accepted by my port restricted NAT as I have now sent packets to it and he connects to me successfully.
STUN and Symmetric NAT
- My console with IP address 192.168.0.1 hosts a game using port 57433. It connects to xbox live to advertise this information.
- Xbox live (using STUN) detects my public IP address of 56.45.32.5 and public port of 57433 and informs my console of this.
- My console updates this information and advertises these details on xbox live.
- Another person browses xbox live for my game. Once he clicks “join” his console retrieves my public IP address and port and attempts to connect directly. It tries to connect on 56.45.32.5 with port 57433.
- Like a port restricted NAT the initial connection will be blocked because I haven’t yet sent any data to that console. My console now sends data to the remote console (IP and port learnt through xbox live) but a new mapping is used using port 45654 with source IP 56.45.32.5.
- The information the remote console received from xbox live was that the game is hosted on 57433 but the symmetric NAT opened up the port 45654 for this connection and not 57433. The remote console fails to connect.
4.4. Traversal Using Relays around NAT - TURN
Traversal Using Relays around NAT - TURN is a protocol that assists in traversal of NAT or firewalls for multimedia applications. It is most useful for clients on networks masqueraded by symmetric NAT devices.
STUN provides one way for an application to traverse a NAT. STUN allows a client to obtain a transport address (an IP address and port) which may be useful for receiving packets from a peer. However, STUN may not be work for some kind of NAT, for example Symmetric NAT. TURN can resolve this problem by relaying data through a server that resides on the public Internet.
Both peer try to set up direct communication between peers over UDP. If that fails, they resort to TCP. If that fails, TURN servers can be used as a fallback, relaying data between endpoints. TURN is just used to relay audio/video/data streaming between peers, not signaling data.
TURN servers have public addresses, so they can be contacted by peers even if the peers are behind firewalls or proxies. TURN servers have a conceptually simple task - to relay a stream - but, unlike STUN servers, they inherently consume a lot of bandwidth.
STUN vs TURN
Demilitarized Zone - DMZ is a physical or logical subnetwork that contains and exposes and organization's external-facing services to a usually larger and untrusted network, usually the Internet.
DMZ acting as a gateway to the public Internet, is neither as secure as the internal network, nor as insecure as the public internet.
Hosts in the DMZ are permitted to have only limited connectivity to specific hosts in the internal network, as the content of DMZ is not as secure as the internal network.
Communication between hosts in the DMZ and to the external network is also restricted, to make the DMZ more secure than the Internet, and suitable for housing these special purpose services. This allows hosts in the DMZ to communicate with both the internal and external network, while an intervening firewall controls the traffic between the DMZ servers and the internal network clients, and another firewall would perform some level of control to protect the DMZ from the external network.
Some services in the DMZ: Web servers, Mail servers, FTP servers, VoIP servers.
There are many different ways to design a network with a DMZ. Two of the most basic methods are with a single firewall, and with dual firewalls.
Single firewall
Dual firewall
6. Reference
Traversal Using Relays around NAT - TURN is a protocol that assists in traversal of NAT or firewalls for multimedia applications. It is most useful for clients on networks masqueraded by symmetric NAT devices.
STUN provides one way for an application to traverse a NAT. STUN allows a client to obtain a transport address (an IP address and port) which may be useful for receiving packets from a peer. However, STUN may not be work for some kind of NAT, for example Symmetric NAT. TURN can resolve this problem by relaying data through a server that resides on the public Internet.
Figure 12. P2P applications with TURN
This diagram shows TURN in action: pure STUN didn't succeed, so each peer resorts to using a TURN server.Both peer try to set up direct communication between peers over UDP. If that fails, they resort to TCP. If that fails, TURN servers can be used as a fallback, relaying data between endpoints. TURN is just used to relay audio/video/data streaming between peers, not signaling data.
TURN servers have public addresses, so they can be contacted by peers even if the peers are behind firewalls or proxies. TURN servers have a conceptually simple task - to relay a stream - but, unlike STUN servers, they inherently consume a lot of bandwidth.
STUN vs TURN
- If STUN is used, media will travel directly between both endpoints, whereas media will be proxied through the server if TURN is utilized.
- TURN is preferred because it is capable to traverse symmetric NATs. However, STUN is useful to speedup the connection out of getting immediate candidates when users are sitting behind same NAT.
- When we use both STUN and TURN servers, STUN is always attempted first, TURN is used as fallback option depending on client locations and network topologies.
- TURN protocol runs top of STUN to setup a relay service.
- A critical disadvantage of a TURN server is its costs, and huge bandwidth usage in case when HD video stream is delivered.
Demilitarized Zone - DMZ is a physical or logical subnetwork that contains and exposes and organization's external-facing services to a usually larger and untrusted network, usually the Internet.
DMZ acting as a gateway to the public Internet, is neither as secure as the internal network, nor as insecure as the public internet.
Hosts in the DMZ are permitted to have only limited connectivity to specific hosts in the internal network, as the content of DMZ is not as secure as the internal network.
Communication between hosts in the DMZ and to the external network is also restricted, to make the DMZ more secure than the Internet, and suitable for housing these special purpose services. This allows hosts in the DMZ to communicate with both the internal and external network, while an intervening firewall controls the traffic between the DMZ servers and the internal network clients, and another firewall would perform some level of control to protect the DMZ from the external network.
Some services in the DMZ: Web servers, Mail servers, FTP servers, VoIP servers.
There are many different ways to design a network with a DMZ. Two of the most basic methods are with a single firewall, and with dual firewalls.
Single firewall
Figure 13. Single firewall DMZ
A single with at least 3 network interfaces can be used to create a network architecture containing a DMZ. The external network is formed from the ISP to the firewall on the first network interface, the internal network is formed from the second network interface, and the DMZ is formed from the third network interface. The firewall becomes a single point of failure for the network and must be able to handle all of the traffic going to the DMZ as well as the internal network.Dual firewall
Figure 14. Dual firewall DMZ
The more secure approach is to use two firewalls to create a DMZ. The first firewall must be configured to allow traffic destined to the DMZ only. The second firewall only allows traffic from the DMZ to the internal network. One of the drawbacks of this architecture is that it's more costly, both to purchase and to manage.
DMZ host
Some home routers refer to a DMZ host. A home router DMZ host is a single address on the internal network that has all traffic sent to it which is not otherwise forwarded to other LAN hosts. By definition this is not a true DMZ, it does not separate the host from the internal network.
[1] https://en.wikipedia.org/wiki/Traversal_Using_Relays_around_NAT
[2] https://en.wikipedia.org/wiki/STUN
[3] http://www.cisco.com/c/en/us/about/press/internet-protocol-journal/back-issues/table-contents-29/anatomy.html
[4] https://en.wikipedia.org/wiki/Network_address_translation
[5] https://www.grc.com/nat/nat.htm
[6] http://superuser.com/questions/284051/what-is-port-forwarding-and-what-is-it-used-for
[7] https://www.think-like-a-computer.com/2011/09/19/symmetric-nat/
[8] http://www.html5rocks.com/en/tutorials/webrtc/infrastructure/
[9] Chapter 4, Network Layer, Computer Networking: A Top Down Approach, 6th edition, Jim Kurose, Keith Ross
[10] Slide NAT, CS 4700/CS 5700 Network Fundamentals course













Không có nhận xét nào:
Đăng nhận xét